Successful network defenders are rewriting the conventional rules of information security, changing how they approach basic principles of confidentiality, integrity, and availability.
The successful defenders don’t think about stopping attacks alone. They also look for ways to understand attacker behaviour and adopt tactics to make it harder for attackers to achieve their goals, John Lambert, general manager of Microsoft’s Threat Intelligence Centre, said at the recent Kaspersky Lab Security Analyst Summit. They maximise learning opportunities and look for trusted peers to share information.
“They’re discarding stuff that doesn’t work…. And stuff they don’t have, they’re inventing it,” said Lambert.
Traditionally, network teams are urged to focus their energies on understanding what assets they have in their environments, developing incident response plans for when things go awry, and treating penetration tests as report cards on the state of their security defences. They make lists of things that are important in their network environments, such as domain controllers, administrator accounts, and certificates. As a result, they are “awash in lists,” Lambert said.
Many of them are encouraged to keep what they know about specific incidents and what they observed in their environments to themselves because sharing threat indicators is seen as giving away competitive advantage. Modern defenders cannot afford to keep doing things this way, Lambert said.
Think in graphs
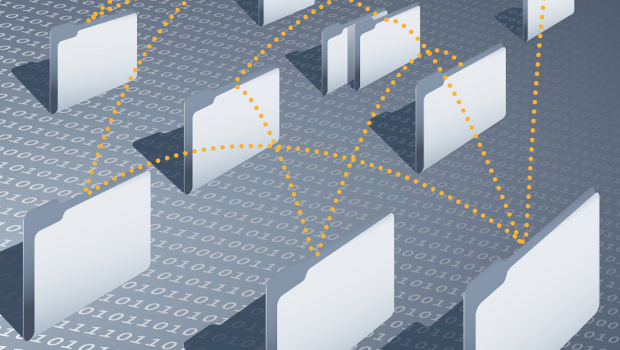
Instead of drawing up lists, network defenders need to think in graphs to understand network edges and dependencies. For example, instead of simply creating a list of sensitive accounts, they create a diagram showing which servers the account can log into, and what other servers are accessible from that server, and keep going until they have a web showing the impact each account has on the network. The one with the most connections is the one with the most impact if it is ever compromised, so it should be viewed as the “god account.” Without this graph, it’s difficult to understand how a sole laptop connected to a system in accounting can have an impact on the rest of the environment, Lambert said.
This exercise also uncovers situations where credentials being reused create links between unrelated machines. Malware can also create edges where none existed before as it traverses the network.
For example, instead of listing all the assets and their IP addresses, defenders can create a graph showing how many other assets one machine with an account is connected to. As the list includes more accounts and machines, the web becomes even more interconnected and intricate, but it immediately locates the network edge and identifies the god accounts that can cause the most damage.
“Modern defenders, they have a graph of things to protect,” Lambert said. “They think about adversaries and their next move.”
Attackers rely on graphs, so instead of focusing on specific incidents, modern defenders should learn what tools, techniques, and procedures adversaries are using. Rather than looking at logs, they rely on analytics gathered internally and hunt for clues using tools like Yara to find network edges and nodes. Yara uncovers patterns in files, systems, and networks, so analysts write Yara rules to find, group, and categorise related files and find connections.
Network defenders also need to find all the backdoors and malware the attackers are using. The network team may have found and removed two backdoors, but if they miss a third one, then the team’s job is far from done.
Share and learn together
Threat intelligence helps defenders capture the attacker graph by showing what intrusions in other networks looked like. Traditional approaches focus on what the attackers are doing right now, but that’s too limiting. Defenders need to see what attackers have done in the past, Lambert said.
This is happening more often as information sharing becomes more accepted within the industry. There is no magic or secret sauce on how threat data gets shared, as it’s primarily trust-based. It is a mutually beneficial relationship because sharing indicators — things the defender knows — help researchers uncover more useful information. Modern defenders share information across geographies, industries, and even with competitors.
“They [defenders] find trusted peers in the community, and understand the importance of learning from others and their practices,” Lambert said. “You have to get to know people, you’re not trading with a vendor, you’re sharing with a person.”
Modern defenders also understand that the goal is not only to get attackers off the network and block attempts, but also to make it more expensive to launch the campaigns in the first place. Cooperation leads to important research being published and shared. That encourages more researchers to look at the problem and come up with more insights and answers. The resulting publicity can lead to attack infrastructure being shut down and defenders receiving improved tools.
If adversaries have to go back and beef up their development efforts, it slows down the attack timeline.
“The goal should be to remove all of us from a world of information silos and not sharing, to a world where hacker activity is imprisoned and all their OpSec mistakes are trapped and can’t be used anymore,” Lambert said.
Time to wake up
Defenders have to look for nodes so that they can destroy the graph, Lambert said. They can rewrite the edges and nodes by creating their own versions of man-in-the-middle attacks and sinkholes to divert malicious traffic.
Attackers do not think in lists, and defenders don’t think in graphs. As long as defenders continue to focus on lists, they will continue to lose.
“In the world of cyber, nothing gets better until the victims wake up,” Lambert said.
IDG News Service





Subscribers 0
Fans 0
Followers 0
Followers